
In an era where data is the new currency, safeguarding sensitive information has become a mission-critical priority for businesses of all sizes. The rise of remote work, cloud adoption, and increasingly sophisticated threat vectors has blurred the boundaries of traditional security perimeters. As a result, Data Loss Prevention (DLP) is no longer a luxury—it’s a necessity.
This blog explores why DLP should be a core component of every organization’s cybersecurity strategy, focusing on technical benefits and implementation realities.
Understanding DLP: A Quick Recap
Data Loss Prevention (DLP) is a framework for detecting and preventing the unlawful use, transmission, or exposure of sensitive data, whether structured or unstructured.
Modern DLP solutions operate on three main layers:
•Data at Rest—Identifies and safeguards sensitive information stored on endpoints, servers, databases, and cloud storage.
•Data in Motion—monitor network activity (email, web, FTP, etc.) to detect data exfiltration efforts.
•Data in Use—Controls and analyzes endpoint behaviors including copy-paste, print, screen capture, and USB usage.

Why Every Organization—Big or Small—Needs DLP?
1. Data Visibility across the Enterprise
Security teams cannot safeguard what they do not see. One of the most significant advantages of DLP is data detection and classification. A well-developed DLP system is compatible with file servers, endpoints, and cloud services.
•Locate sensitive information (PII, PHI, PCI, source code).
•Use content-aware regulations based on file signatures, keywords, regular expressions, and fingerprints.
•Classify data based on its sensitivity level using metadata tagging or automatic classification algorithms.
This visibility lays the groundwork for granular policy enforcement.
2. Policy Enforcement and Real-Time Controls
DLP is more than just alerting; it is also about preventative enforcement. Policies can be specified as follows:
•Restrict, quarantine, or encrypt data flows.
•Redact specific content from papers.
•Inform security personnel or integrate with SIEM/SOAR systems for incident response.
•Automatically enforce measures such as file tagging, encryption, and upload restriction.
For example, a corporation can set up a policy that stops emails containing credit card data from being forwarded to non-corporate domains or preventing source code from being uploaded to GitHub.
3. Insider Threat Detection
Insider threats are more difficult to identify than external threats, whether a dissatisfied employee steals data before leaving or a contractor misuses business files.
DLP detects anomalies by monitoring user activity and applying context-aware rules.
•Transfer large files to USB devices.
•Use personal email or cloud storage at unusual hours.
•Attempts to access critical folders outside of role-based access.
Some solutions interface with UEBA (User and Entity Behavior Analytics) to enable enhanced risk scoring and correlation.
4. Support for Hybrid and Multi-Cloud Environments
DLP has progressed beyond the old perimeter-based solutions. Leading solutions are currently offering:
•Endpoint DLP: Applying policies to user devices, including offline protection.
•Cloud DLP: API-driven interaction with SaaS applications such as Microsoft 365, Google Workspace, and Salesforce.
•Network DLP: Monitoring traffic at the perimeter or through virtual appliances in the cloud.
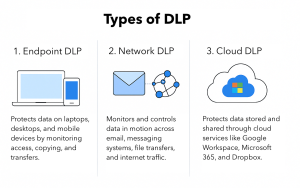
This multi-channel coverage is crucial in hybrid situations where data is shared between on-premises, cloud, and personal devices.
5. Compliance Automation
As regulatory requirements get harder and more complicated, DLP assists firms in mapping controls directly to compliance demands, such as:
•GDPR: Preventing the unlawful transmission of EU citizens’ data.
•HIPAA: Protecting electronic protected health information (ePHI).
•PCI DSS: securing cardholder data.
•Examples include CCPA, ISO 27001, and NIST.
Auditable logs, real-time alarms, and reporting dashboards make compliance easier and audits more efficient.
6. Reducing Human Error
Human error is the most common cause of data leaks—sending files to the incorrect person, attaching the wrong document, or misusing cloud tools.
DLP can introduce adaptable, contextual stimuli such as
•”You’re about to send a file with SSNs. “Do you want to proceed?”
•Automatic redaction or encryption of critical attachments.
•Preventing unintentional uploads to unauthorized apps.
This reduces risk while ensuring that corporate operations continue uninterrupted.
Final Thoughts
A DLP system is valuable not only for data security, but also for control, visibility, and operational trust. Whether you’re managing intellectual property, customer information, financial data, or HR files, DLP gives you a centralized solution to monitor, regulate, and secure your data across every endpoint, channel, and user.
As threats evolve and rules tighten, DLP is no longer optional—it is required.

